It’s the Data Privacy Officer’s nightmare: receiving an enforcement action or legal challenge based on personal information processing that no one even knew was happening. All of the activities for data mapping, auditing data activities across business functions, and conducting vendor risk assessments … yet still there is something that went unidentified. All too often this happens in the area of data collection and processing on an organization’s website due to the behavior of tag piggybacking.
Piggybacking tags or pixels are when one third-party platform loading on a website loads or injects into the page a script for another platform. This results in the additional third-party loading, collecting consumer data, and setting cookies on the user’s browser.
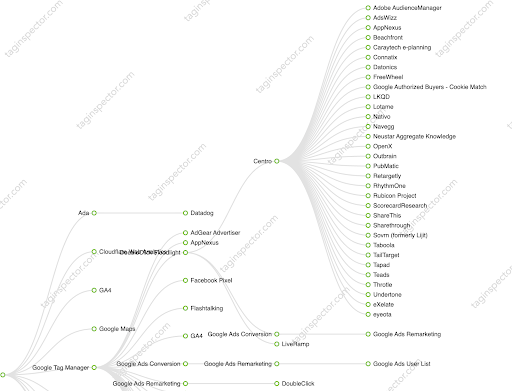
The danger with piggybacking tags is that in a majority of cases, no one in the organization even knows the behavior is happening. That which we do not know, we miss when considering and implementing privacy compliance protections.
Tag piggybacking is very common when working with advertising platforms implemented on a website. Often the behavior facilitates “cookie matching”, or the sharing of unique personal and device identifiers, across various advertising technologies to aid in targeted advertising. Let’s review some common privacy concerns that result from piggybacking tags.
Unauthorized Sale/Share of Personal Information
The most common reason why tag piggybacking occurs is to facilitate “cookie matching” across platforms. First, piggybacking is a clear indication that the purpose for the initial data collection is for targeted advertising. As a result, consent and user choice considerations must be taken. Further, the piggybacking behavior is indicative of the sharing of personal information across platforms, which must be considered for further user notification and choice. All too often organizations will state in their privacy notice that no sale or sharing of personal information is occurring on the website only for piggybacking behavior to clearly indicate otherwise.
Introduction of Wiretapping Risk
As previously explained in our risk review for wiretapping risk, several U.S. states have laws that private litigators are using to bring actions against organizations concerning their use of tracking technologies on websites. In some cases, the tags being piggybacked or loaded are platforms that have functionality for session recording and heat mapping.
In 2024, a common behavior witnessed on websites was the piggybacking of a platform named “Clarity” via the Microsoft Universal Events Tracker. Clarity is a session recording and heat mapping tool that can help with analytics. While the use of such a platform could be ok if known and accounted for, the piggybacking behavior has gone unnoticed across thousands of websites. Organizations must understand this piggybacking behavior in order to mitigate potential compliance risks.
Lack of User Notice
As piggybacking tags are often unnoticed, they represent “unknown unknowns” for an organization. As such, no risk assessments are conducted, processing behavior is not understood, and notices for users are not updated to cover the additional data processing by the injected platforms. With an increased focus by enforcement agencies around consumer misrepresentations stemming from inaccurate privacy information, these “unknown unknowns” can become a significant risk.
Data Leakage
Beyond the direct privacy compliance risk, piggybacking tags are also being provided information about an organization’s consumers. This can include the pages they view and the interactions they make with the website. As more and more organizations are investing in their first-party data architectures and on new user acquisition, the fruits of these investments are being stolen as a result of piggybacking tags.
To address all privacy compliance considerations stemming from the collection and usage of consumer data on websites, it is critical to understand all platforms loading and what information they are collecting. Piggybacking tags represent opaque data collection that introduces compliance risk when present. It is important to run regular website compliance risk assessments with platforms like Tag Inspector to ensure all platforms loading on a website have been vetted with appropriate compliance considerations taken.

